How VREM solutions
- VREM and Encrypting for data classification: VREM partners with Encrypting to enable end-to-end data security. Encrypting’s Data Security Fabric solution simplifies data governance, security, and workflow management for sensitive data (structured, unstructured, and semi-structured) across multicloud and hybrid environments.
Data discovery
To facilitate data discovery, VREM has partnered with affiliates and partners to help organizations securely protect data on a large scale. Both enterprises and individuals need to first find and classify data to determine if it is sensitive. After all, you cannot protect what is unknown. With the transition to cloud, multi-cloud, and hybrid environments, finding sensitive data has become even more challenging. Enterprises and individuals now require a more granular level of data security, which includes locating all data, classifying it, and providing appropriate levels of protection.
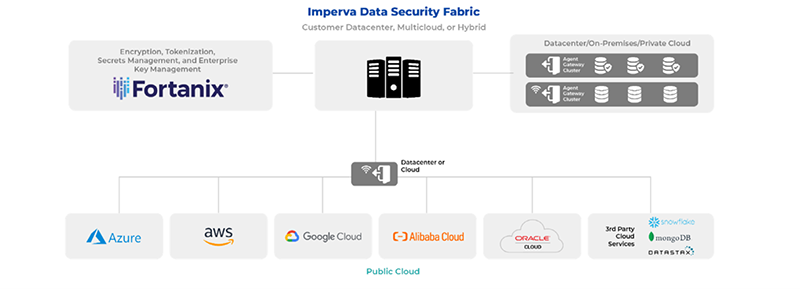
VREM Enterprise Key Management
The VREM data security and privacy platform simplifies the management of data and keys across hybrid multicloud environments. VREM enables users to unify the management of crypto keys and services into a single system of record to help deploy universal encryption of data, wherever it is.
This centralized solution implements a consistent and fine-grained key access policy based on Role-Based Access Control (RBAC).In addition, the platform enables administrative safeguards with multiple approval requirements for high-impact administrative actions such as deleting keys. Centralized policy enforcement reduces risk and simplifies compliance audits. Achieve non-repudiation in audits with immutable logging that integrates seamlessly with SIEM solutions.

Data categorization
Zero trust requirement
| ZTMM requirement | What it entails | Required capabilities |
|---|---|---|
| Data categorization | Automate data categorization and labelling enterprise- wide with robust techniques; granular, structured formats; and mechanisms to address all data types. |
|
- VREM provides an end-to-end solution for data discovery, classification, and tokenization.
- VREM’s Data Masking and Tokenization: VREM’s tokenization helps organizations shift-left the encryption of sensitive data. Tokenization encrypts all sensitive data in a database, but in a way where people and analytical tools can still search and find meaning in the data. After tokenization, it is easy and secure to share the data further.
Data classification
The Data Security Fabric (DSF) discovers, classifies, and protects file systems and data. It employs a combination of data science, machine learning, and behavioral analytics to provide real-time protection of data repositories against internal and external threats, monitoring user activity and alerting the data security team about suspicious behaviors that exceed normal user behavior patterns.
Through the DSF solution, customers can discover and classify where sensitive data is located. Once sensitive data is identified, enterprises can protect it through encryption and tokenization using the VREM Data Security Manager.
Tokenization
Tokenization, or format-preserving encryption, is a game-changer in implementing zero trust security for data, as it enables granular data access control as early as possible in the data’s lifecycle. Tokenizing data makes security an attribute of the data, abstracting it from legacy infrastructure security.
Tokenization encrypts all sensitive data in a database, but in a way where people and analytical tools can still search and find meaning in the data. The encrypted data keeps the same length, character set, and format so that for example, a credit card number, or social security number is still recognized as such, but the original value is partially obscured. You can also selectively encrypt sensitive fields within a database without impacting the database schema.
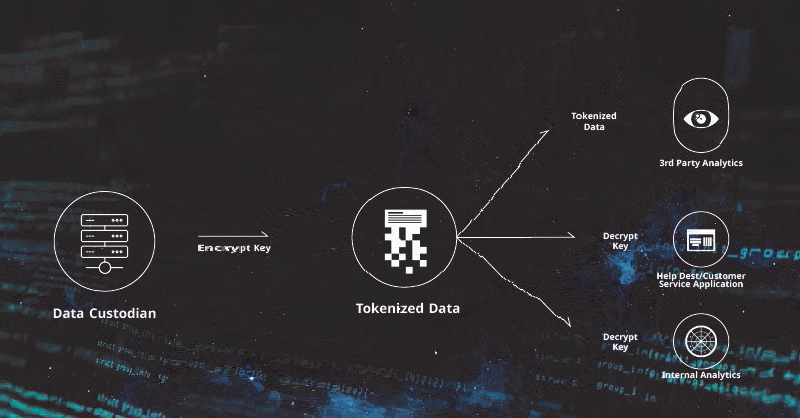
Tokenized data can be shared with 3rd parties or used internally, using different detokenization policies, depending on the application. VREM supports quorum control, where multiple admins must approve high-privilege actions such as viewing full original data.
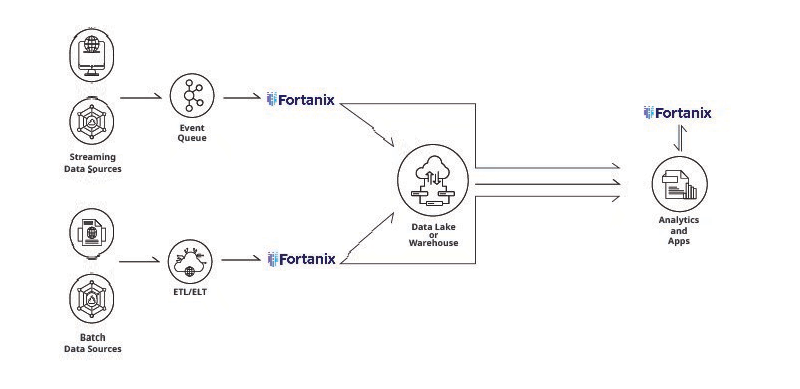
When organizations have many different data sources and pipelines, it is more practical to apply tokenization to ingested data during integration processes such as ETL or ELT, or during write operations to the data store, using the data store’s User-Defined Functions (UDFs). This approach ensures consistent tokenized data that is transparent to other apps.
VREM tokenization offers granular controls over data and ensures that access to it is based on user identity. This aligns with the crux of zero trust, which is around secure access andensuring that only authorized users have access.