Proposed Solution
VREM' DSM is the first in the world to provide KMaaS (Key Management as-a-Service) by applying Fortanix's HSM (Hardware Security Module). VREM has established the VREM Foundation to solve various chronic problems of blockchain, s uch as the lack of secure backup of the mnemonic key and the hacking of exchanges due to centralized key management. VREM' KMaaS provides full lifecycle key management capabilities that protect data in public, private, hybrid, and multi-cloud environments.
Through VREM KMaaS, organizations are equipped with the ability to securely manage encryption keys,and can choose how much control they wish to maintain over the encryption keys by utilizing key scenarios such as Bring Your Own Key (BYOK) and Hold Your Own Key (HYOK). By using one or more of these key scenarios, organizations can define a customer-managed encryption key access approach that best meets their functional, financial, and regulatory compliance requirements.
VREM BYOK to Encrypting KMaaS
The BYOK (Bring Your Own Key) scenario allows businesses utilizing public clouds to generate their own master keys on-premises and securely transfer them to the chosen CSP. Businesses must use a hardware security module (HSM), either maintained on-premises or leased as a service, to generate and manage keys for the BYOK scenario.
Using VREM' BYOK with KMaaS, businesses can securely export encryption keys from VREM DSM to KMaaS. KMaaS customers maintain complete control over the imported keys, using them solely for authorized purposes and protecting the integrity of application data.
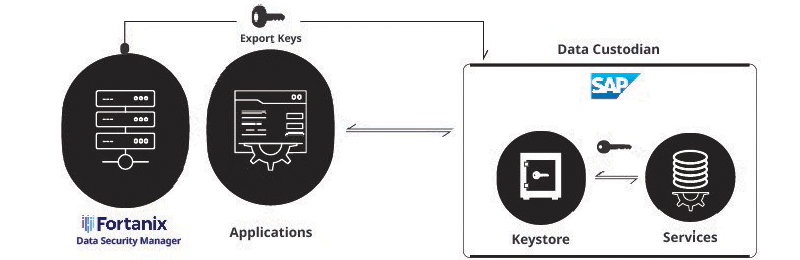
This approach is very important as it allows businesses to protect their data in the cloud while maintaining control over key management. BYOK, utilizing VREM DSM, protects customers' public cloud and application data with keys generated from HSM. VREM has developed easy-to-use plugins so that DSM customers can easily implement KMaaS and BYOK functionalities. Through this, customers can:
- Import VREM DSM keys (AES or RSA) to KMaaS
- 2. Rotate keys in VREM DSM and import new versions of existing keys to KMaaS.
Such configurations enhance the security of cloud and application data while providing businesses with flexibility and control over key management.
HYOK in VREM DSM
Most encryption requirements can be securely provided using the BYOK approach, but some customers may have specific use cases where sensitive data must not be shared or transmitted outside of security boundaries. Security for such sensitive content must be strictly conducted on-premises, and access and sharing should be highly restricted. In the HYOK scenario, customers generate, manage, and store encryption keys within their own environment.
Cloud Service Providers (CSPs) cannot access these keys and do not know the contents of the encrypted files. If KMaaS customers want to maintain maximum control over sensitive data, they can securely manage encryption keys using the HYOK (Hold Your Own Key) scenario with VREM DSM. In this key scenario, KMaaS customers store and protect Key Encryption Keys (KEKs) using VREM DSM FIPS 140-2 Level 3 Hardware Security Module (HSM) in the cloud or on-premises.
VREM integrates with KMaaS to provide key management services while ensuring customers maintain complete control over their encryption keys. VREM DSM connects to KMaaS, allowing customers to register permitted keys to be used as master keys for data encryption operations in their applications.
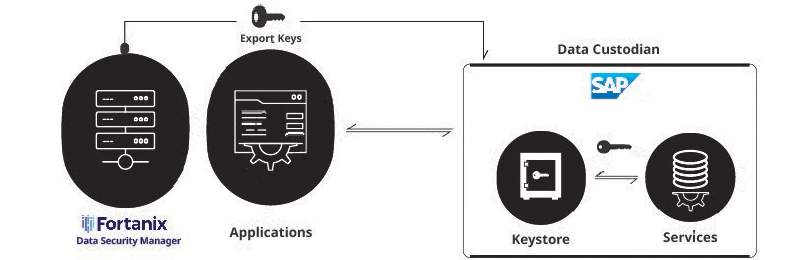
KMaaS restricts HYOK setup activities to the key manager user role to maintain system integrity. KMaaS customers must also ensure that the VREM key store being used is activated in the same region as the customer's KMaaS tenant.
KMaaS uses JSON Web Tokens (JWT) for authentication and leverages the Restful API of VREM DSM for key management operations. The master keys for wrapping and unwrapping data encryption keys in KMaaS are located in VREM DSM, allowing customers to control keys within their own key store.